Invoking secure web services using SOAPUI - part1
SOAPUI is a very useful free tool which can be used in SOA testing. Service invocation using SOAPUI is straight forward and you can find a lot of references by surfing web. However, there are limited information about invoking services with various QOS (Quality of Service) features such as WS-Security, WS-Addressing etc.
Click on Security link and Select "Enable Security" option. Then select, UserNameToken security scenario.
In the next screen, select admin user group and click on finish to apply the security policy for HelloService.
Step 2
We have configured server side security policy. If you look at the WSDL of HelloService (http://localhost:9763/services/HelloService?wsdl), you will notice that UserNameToken security policy is added to the service.
Now, we need to configure SOAPUI project to talk to HelloService with the required user credentials.
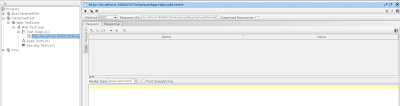
First, start SOAPUI and create a new project. Specify https://localhost:9443/services/HelloService?wsdl as the initial WSDL. Keep the other default settings.
You will see the following project structure.
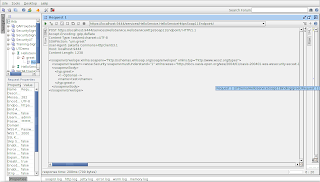
Replace ? with an input value in the request editor and run the test. You will encounter a SOAPFault, Missing wsse:Security header in request, since we did not send security headers with the request.
Lets configure client side security now. In the Request Properties pane of SOAPUI project, you will find the following properties.
Username
Password
WSS-Password Type
WSS TimeToLive
Specify the following values for the above properties.
Username = admin
Password = admin
WSS-Password Type = PasswordText
WSS TimeToLive = 2000
Run the test. Have a look at the raw request view. You will see security header is added to the request.
Thats all! We will look at more advanced scenarios such as signing and encrypting messages with SOAPUI in future posts.
This post takes you through the simplest QOS scenario, a web service is secured with UserName token policy and how SOAPUI is used to invoke such a service.
I will use the default HelloService hosted in WSO2 WSAS in this demonstration but the service invocation approach is similar with any service provider.
Pre-requisites:
1. Download and install SOAPUI-3.6.1 or later (free version)
2. Download and install WSO2 WSAS-3.*
Step 1
First, we need to secure a web service hosted in WSAS. We will configure HelloService so that only the users in admin group will be allowed to invoke the service. In order to do that, start WSO2 WSAS and log in to management console. Then, select HelloService from Deployed Services page.
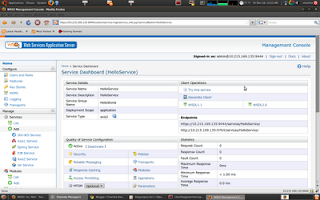
You will be directed to the service dashboard of HelloService as follows.

Click on Security link and Select "Enable Security" option. Then select, UserNameToken security scenario.

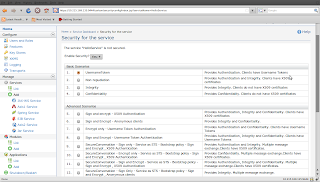
In the next screen, select admin user group and click on finish to apply the security policy for HelloService.
Step 2
We have configured server side security policy. If you look at the WSDL of HelloService (http://localhost:9763/services/HelloService?wsdl), you will notice that UserNameToken security policy is added to the service.
Now, we need to configure SOAPUI project to talk to HelloService with the required user credentials.
First, start SOAPUI and create a new project. Specify https://localhost:9443/services/HelloService?wsdl as the initial WSDL. Keep the other default settings.
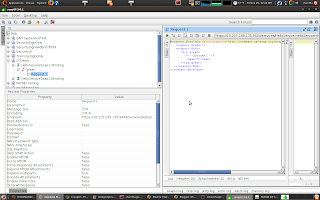
You will see the following project structure.

Replace ? with an input value in the request editor and run the test. You will encounter a SOAPFault, Missing wsse:Security header in request, since we did not send security headers with the request.
Lets configure client side security now. In the Request Properties pane of SOAPUI project, you will find the following properties.
Username
Password
WSS-Password Type
WSS TimeToLive
Specify the following values for the above properties.
Username = admin
Password = admin
WSS-Password Type = PasswordText
WSS TimeToLive = 2000
Run the test. Have a look at the raw request view. You will see security header is added to the request.
Thats all! We will look at more advanced scenarios such as signing and encrypting messages with SOAPUI in future posts.


Comments
Neda
eviware.com
Neda
eviware.com
Neda
Eviware.com
- XML Signature
- XML Encryption
- username token
together, i experiment some problems testing with soapui/Wso2